The World of Hackers: A Fascinating Journey
As technology continues to advance at a rapid pace, so does the prevalence of hackers in our digital world. These individuals possess a unique skill set, allowing them to exploit vulnerabilities and gain unauthorized access to various systems. However, not all hackers are created equal. In fact, there are several distinct types of hackers, each with their own motivations and goals.
The White Hats: Ethical Hackers
White Hat hackers, also known as ethical hackers, dedicate themselves to finding vulnerabilities in systems and networks to help organizations enhance their security. Equipped with an in-depth knowledge of digital systems, these individuals work closely with companies to identify and fix potential weaknesses before malicious hackers can exploit them. White Hat hackers often use their skills for the greater good, working as cybersecurity consultants or members of specialized teams.
Contrary to popular belief, ethical hacking is a legitimate profession that requires extensive training and certifications. These hackers adhere to strict ethical guidelines and always seek permission before assessing the security of a system. Their expertise is invaluable in safeguarding businesses from cyber threats, making them an integral part of the digital landscape.
The Black Hats: The Dark Side of Hacking
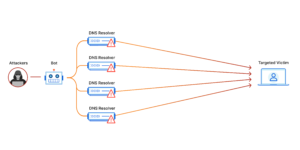
Black Hat hackers, on the other hand, are malicious individuals who use their skills for personal gain or to cause harm. Their motivations can vary, ranging from financial gain to political activism or even pure mischief. These hackers are often associated with cybercrime, such as stealing sensitive information, launching denial-of-service attacks, or spreading malware.
Unlike ethical hackers, black hat hackers operate outside the boundaries of the law. They exploit vulnerabilities without permission and are constantly on the lookout for systems they can compromise. Cybersecurity professionals and law enforcement agencies work tirelessly to track down these individuals and bring them to justice.
The Gray Area: The Gray Hats
In between the black and white hats lie the Gray Hats. These hackers don’t fit neatly into either category, as their motivations and actions can be ambiguous. Gray hat hackers may discover vulnerabilities and exploit them without malicious intent, but without seeking permission either. Some may even choose to notify the affected party after exposing the vulnerability.
While their actions may not always be legal, gray hat hackers often have good intentions and aim to draw attention to security flaws that need addressing. Their methods may be unconventional, but they can play a role in improving overall cybersecurity by highlighting weaknesses that would have otherwise gone unnoticed.
Conclusion
The world of hackers is complex and diverse, with individuals falling into different categories based on their intentions and actions. Ethical hackers offer their expertise to safeguard businesses, while black hat hackers pose a threat to digital security. Gray hat hackers occupy a morally ambiguous space, sometimes helping, sometimes causing disruption.
Understanding the different types of hackers is crucial in combatting cyber threats and protecting sensitive information. By working together with ethical hackers and implementing robust security measures, businesses can stay one step ahead of the black hats and gray hats, ensuring a safer digital landscape for all.