Introduction
Running a website or an online business can be a rewarding experience, but it’s crucial to be aware of the various cyber threats lurking in the digital world. One such threat that every website owner should be familiar with is the Denial of Service (DOS) attack. In this blog post, we will delve into the concept of DOS attacks, explore common examples, discuss preventive measures, and provide insights on mitigating the effects of such attacks.
What is DOS Attack?
A Denial of Service (DOS) attack is a malicious attempt to disrupt the normal functioning of a website or online service by overwhelming it with an excessive amount of traffic or requests. The goal of a DOS attack is to make a website or service unavailable to its intended users, causing inconvenience, loss of revenue, and damage to reputation.
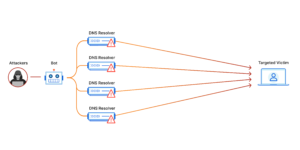
There are several types of DOS attacks, including TCP/IP, HTTP, and DNS floods. TCP/IP attacks aim to exhaust the network resources of a target by sending a flood of TCP or IP packets, while HTTP attacks overload a server by flooding it with HTTP requests. DNS floods target the domain name system servers with an overwhelming number of requests, making it impossible for legitimate users to access the intended website.
Common Examples of DOS Attack
One common example of a DOS attack is the Ping of Death, where an attacker sends an oversized ping packet to a target computer. This causes the target system to crash or become unresponsive. Another example is the SYN flood attack, which exploits the vulnerability in the TCP three-way handshake process, overwhelming the target system with incomplete connection requests.
Another widespread example is the Distributed Denial of Service (DDoS) attack, where multiple compromised computers known as botnets are used to flood the target system with traffic. These botnets can consist of hundreds or even thousands of devices, making it incredibly difficult to mitigate the attack.
Preventative Measures of DOS Attack
While it’s impossible to completely eliminate the risk of a DOS attack, there are several preventive measures that website owners can take to minimize the likelihood of an attack and protect their online presence. Firstly, implementing a robust firewall and intrusion detection system (IDS) can help filter out malicious traffic. Additionally, regularly patching and updating software and operating systems can address any vulnerabilities that attackers may exploit.
Furthermore, limiting resource consumption per user, setting up rate limiting, and using traffic analysis tools can help identify and block suspicious traffic patterns. It’s also recommended to work closely with a reliable hosting provider that has built-in DOS protection mechanisms and can assist in case of an attack.
How to Mitigate the Effects of a DOS Attack
If your website becomes a victim of a DOS attack, it’s essential to act swiftly to mitigate its effects. Firstly, you should isolate your affected server or network segment to contain the attack and minimize its impact on other systems. It’s also crucial to monitor network traffic and identify the attacking IP addresses.
In some cases, it might be necessary to contact your Internet Service Provider (ISP) and inform them about the attack, as they can potentially block the malicious traffic closer to its source. Utilizing traffic filtering tools and content delivery networks (CDNs) can also help distribute the traffic load and provide additional protection against DOS attacks.
Conclusion
Denial of Service (DOS) attacks can pose significant threats to websites and online businesses. By understanding the concept of DOS attacks, recognizing common examples, and implementing preventative measures, website owners can significantly reduce the risk of falling victim to such attacks. In the event of an attack, quick and effective mitigation strategies can help minimize the impact and restore normalcy to your online operations.