Introduction
Welcome to our blog post where we dive deep into the world of DDoS attacks, shed light on how they work, explore different types of DDoS attacks, provide real-life examples, discuss effective mitigations, and explain the key differences between DoS and DDoS attacks.
How DDoS Attacks Work
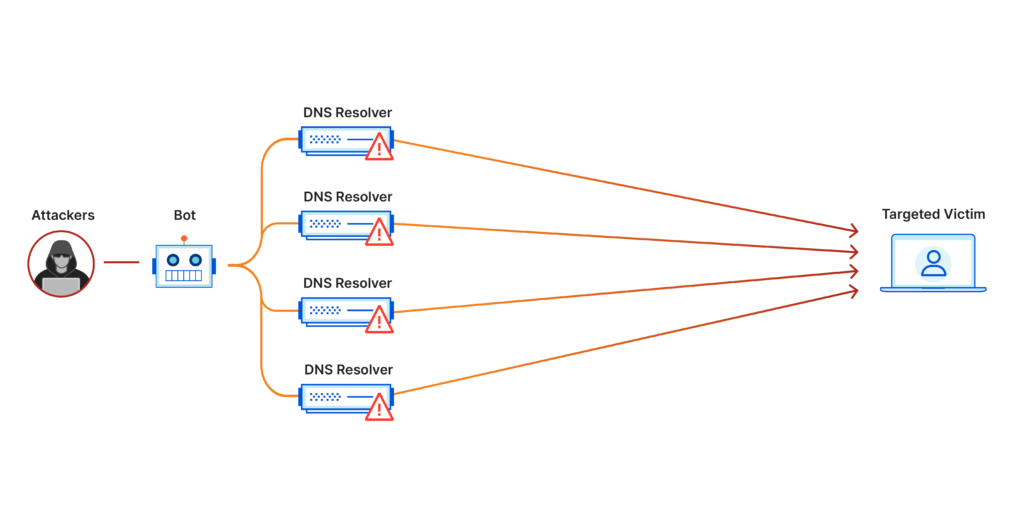
DDoS, short for Distributed Denial of Service, is a malicious attack aimed at disrupting the normal functioning of a targeted network, system, or website by overwhelming it with a flood of traffic, rendering it inaccessible to legitimate users. Unlike a traditional DoS attack, where a single source is used to flood the target, DDoS attacks utilize multiple sources, often compromised computers and devices forming a botnet, to amplify the impact.
There are several techniques employed in a DDoS attack, including:
- UDP Flood: This attack floods the target’s network with User Datagram Protocol (UDP) packets, exhausting its resources and causing service disruption.
- HTTP Flood: In this type of attack, a large number of seemingly legitimate HTTP requests are sent to the target, overwhelming its server resources.
- SYN Flood: The attacker floods the target with a barrage of SYN requests, exhausting its connection resources and preventing legitimate connections.
- ICMP Flood: ICMP Flood involves overwhelming the target with a flood of ICMP Echo Request packets, causing network congestion and potential system crashes.
Examples of DDoS Attacks
- GitHub: In 2018, GitHub was hit by the largest DDoS attack in history, which peaked at an astonishing 1.35 terabits per second. The attack exploited a vulnerability in Memcached servers that allowed the attacker to amplify the traffic.
- Dyn: In 2016, a massive DDoS attack targeted Dyn, a major Domain Name System (DNS) provider. The attack impacted numerous popular websites, such as Twitter, Netflix, and Spotify, rendering them inaccessible to users.
Mitigations against DDoS Attacks
1. Traffic Scrubbing: Implementing a traffic scrubbing solution can help identify and filter out malicious traffic, ensuring that only legitimate traffic reaches the target.
2. Rate Limiting: By setting limits on the number of requests a server can handle from a single IP address, rate limiting can help prevent overwhelming the system.
3. Load Balancing: Distributing traffic across multiple servers or data centres can effectively handle increased traffic and prevent a single point of failure.
4. DDoS Protection Services: Engaging with a reputable DDoS protection service can provide specialized expertise, real-time monitoring, and automated mitigation techniques.
Difference between DoS and DDoS Attacks
The key distinction between a DoS (Denial of Service) attack and a DDoS (Distributed Denial of Service) attack lies in the number of sources used to launch the attack. DoS attacks come from a single source, while DDoS attacks involve multiple sources acting in concert, amplifying the impact on the target.
Conclusion
DDoS attacks continue to pose a significant threat to businesses and organizations, causing financial losses, reputational damage, and disruption of services. Understanding how these attacks work, being aware of different types, implementing effective mitigations, and recognizing the difference between DoS and DDoS attacks are crucial steps towards safeguarding your digital assets and ensuring uninterrupted service for your clients and customers.