Introduction
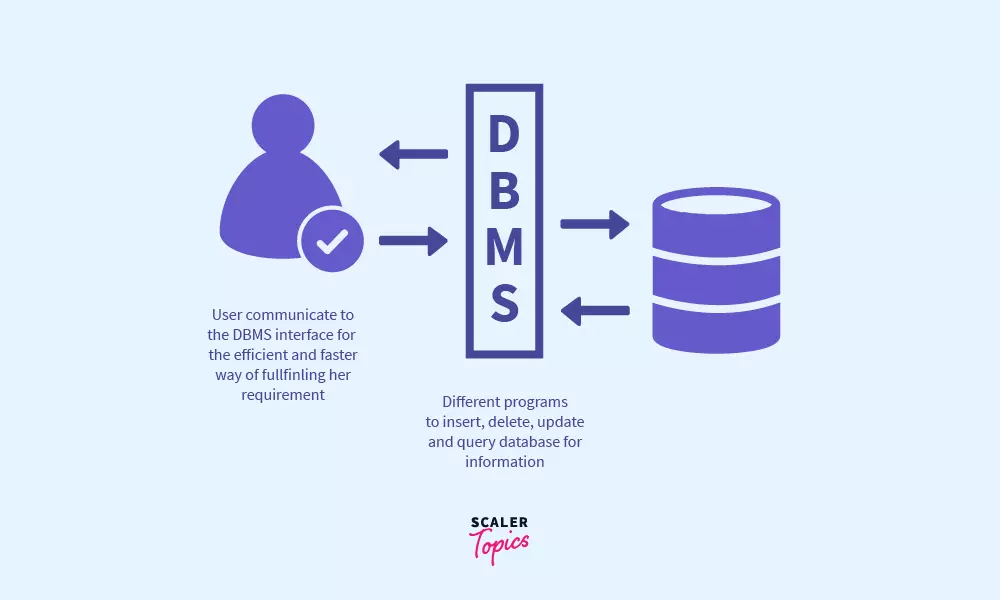
A Database Management System (DBMS) is a software system that allows users to interact with and manage databases. It provides an interface for creating, storing, organizing, retrieving, and managing data efficiently and securely. DBMSs play a crucial role in modern information systems by ensuring data integrity, consistency, and accessibility. Their application spans a wide spectrum, ranging from small personal projects to extensive enterprise systems.
Visualize a world devoid of DBMS: data fragments would sprawl, disconnect, and error susceptibility would prevail. Businesses, organizations, and individuals would struggle to manage their information, making it difficult to make informed decisions, maintain accurate records, or efficiently retrieve relevant data.
DBMS provides a structured setting where data resides in tables, each comprised of rows and columns. This tabular representation enables easy organization and retrieval of data, making it a valuable tool for a variety of applications.Whether you’re tracking customer orders, managing inventory, or analyzing sales trends, a DBMS streamlines these processes. This enables you to focus on deriving insights and making informed decisions.
Key features and functions of a DBMS include
- Data Definition Language (DDL) : Allows users to define the structure of the database, including creating, modifying, and deleting tables, specifying data types, and setting constraints.
- Data Manipulation Language (DML) : Enables users to interact with the data stored in the database. Common DML operations include inserting, updating, deleting, and querying data.
- Data Query Language (DQL) : Provides a way to retrieve specific data from the database using queries. SQL (Structured Query Language) serves as a prevalent language for this endeavor.
- Data Integrity : DBMSs ensure that the data stored in the database is accurate, consistent, and follows predefined rules and constraints. This prevents data corruption and inconsistencies.
- Concurrency Control : Manages concurrent access and modifications by multiple users to the same data, guaranteeing controlled transaction processing for data consistency.
- Security : DBMSs offer mechanisms for user authentication, authorization, and access control to ensure that only authorized users can access and manipulate the data.
- Backup and Recovery : DBMSs provide methods for creating backups of the database and restoring it to a previous state in case of data loss or corruption.
- Scalability : DBMSs are crafted to manage growing data volumes and user demands through features such as replication, partitioning, and clustering support.
- Indexing and Optimization : DBMSs optimize query performance through indexing techniques, query optimization, and caching mechanisms.
- Normalization : The process of organizing data in a structured way to reduce redundancy and improve data integrity.
- Transaction Management : DBMSs support transactions, which are sequences of one or more operations treated as a single unit. This ensures completion of all operations within a transaction or none at all.
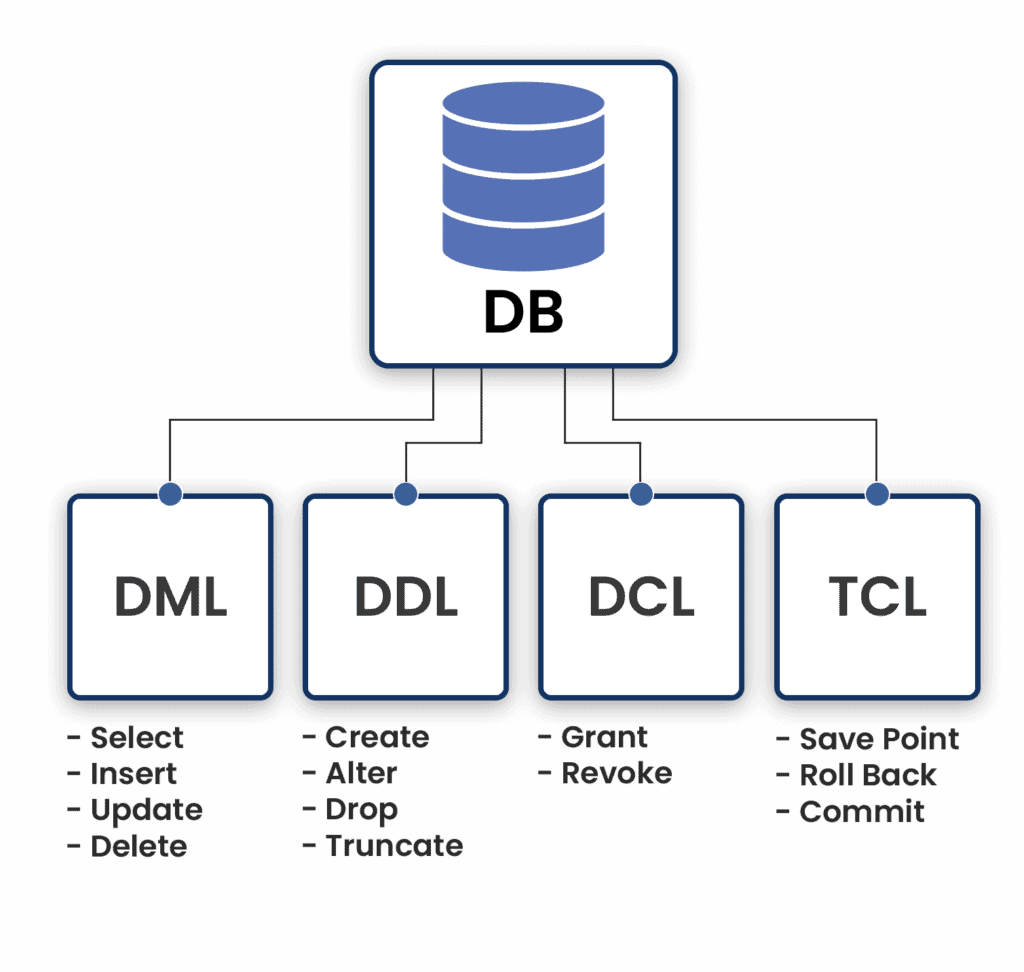
Types of Data Languages
In the context of Database Management Systems (DBMS), data languages primarily refer to the languages used to interact with databases, perform operations, and retrieve information. Here are four frequently used data languages in DBMS.
- Data Definition Language (DDL)
- Data Manipulation Language (DML)
- Data Control Language (DCL)
- Transactional Control Language (TCL)
1. Data Definition Language (DDL)
Data Definition Language (DDL), a subset of SQL (Structured Query Language), centers on defining and overseeing database structure. DDL is utilized to create, modify, and delete database objects like tables, indexes, views, and constraints. It allows database administrators and users to specify the schema of the database, which includes the organization of data, data types, relationships between tables, and integrity constraints.
Key DDL commands include
- CREATE : Used to create new database objects such as tables, indexes, and views. For example:
CREATE TABLE: Defines a new table along with its columns, data types, and constraints.CREATE INDEX: Creates an index on one or more columns to improve data retrieval performance.CREATE VIEW: Defines a virtual table that provides a customized view of the data stored in other tables.
- ALTER : Used to modify existing database objects. Common uses include:
ALTER TABLE: Modifies an existing table by adding, modifying, or dropping columns, constraints, and other properties.ALTER INDEX: Allows modifications to existing indexes, such as adding or removing indexed columns.ALTER VIEW: Changes the definition of an existing view.
- DROP : Used to remove database objects like tables, indexes, or views. For example:
DROP TABLE: Deletes an existing table along with its data.DROP INDEX: Removes an existing index.DROP VIEW: Deletes a view definition.
- TRUNCATE : Removes all rows from a table while keeping the table structure intact. Unlike the DROP command, the TRUNCATE command preserves the table itself.
- COMMENT : Adds comments or documentation to database objects. Comments are useful for providing explanations or context for database elements.
DDL plays a crucial role in ensuring the integrity and organization of a database. It empowers administrators to ensure data consistency, establish table relationships, and apply constraints that avert storage of invalid data. Database administrators or privileged users usually execute DDL statements since they directly affect the database’s structure and organization.
It’s crucial to recognize that DDL statements are generally auto-committed, resulting in immediate, irreversible changes without standard rollback options. As a result, careful consideration and testing are essential when using DDL commands, especially in production environments.
2. Data Manipulation Language (DML)
Data Manipulation Language (DML), a subset of SQL (Structured Query Language), centers on manipulating and retrieving data stored in a database. DML commands facilitate direct interaction with data, enabling users to insert, update, delete, and query records within database tables. DML operations are crucial for maintaining, modifying, and extracting information from a database.
Key DML commands include:
- SELECT : Used to retrieve data from one or more tables. The SELECT statement allows you to specify the columns you want to retrieve and apply filtering, sorting, and grouping to the data. It is the foundation of querying and retrieving information from a database.
- INSERT : Used to add new records (rows) into a table. You specify the target table and provide values for the columns you are inserting data into.
- UPDATE : Used to modify existing records in a table. You specify the target table, set new values for specific columns, and apply conditions to determine which rows to update.
- DELETE : Used to remove records from a table. You specify the target table and apply conditions to identify the rows that should be deleted.
- MERGE (or UPSERT) : Combines INSERT, UPDATE, and DELETE operations based on specified conditions. It allows you to insert new rows or update existing ones depending on whether they already exist.
- CALL (or EXECUTE) : Invokes a stored procedure or a user-defined function to perform specific actions within the database.
- EXPLAIN (or DESCRIBE) : Provides information about how a SQL statement will be executed by the database optimizer. This is helpful for performance tuning.
Application developers, analysts, and users utilize DML operations to engage with data stored in a database. These operations allow for the retrieval of specific information, the modification of existing data, and the addition or removal of records as needed. Proper usage of DML commands is essential for maintaining data accuracy, consistency, and reliability within a database.
It’s important to note that DML operations can affect multiple rows or even entire tables. As a result, care should be taken when executing DML commands, especially in production environments, to avoid unintended data modifications or data loss. Additionally, DML operations are typically performed within transactions to ensure data integrity and consistency.
3. Data Control Language (DCL)
Data Control Language (DCL), a subset of SQL (Structured Query Language), centers on regulating access to data within a database. DCL commands are employed to grant or revoke permissions, administer user access rights, and uphold data security and integrity within a database management system (DBMS).
DCL is essential for maintaining data privacy, security, and ensuring that only authorized users can access and manipulate the data. It allows database administrators to define who can perform specific actions on the database objects.
Key DCL commands include:
- GRANT : Used to give specific privileges or permissions to users or roles. Privileges can include permissions to perform actions such as SELECT, INSERT, UPDATE, DELETE, and more on specific database objects like tables, views, and procedures. For example:
GRANT SELECT, INSERT ON employees TO user1;
- REVOKE : Used to remove specific privileges or permissions from users or roles. This command allows administrators to restrict access that was previously granted. For example:
REVOKE UPDATE ON sales FROM user2;
- DENY : In some DBMSs, there is a DENY command that explicitly denies a specific privilege to a user or role. This is a more restrictive form of revoking access.
DCL commands help establish a robust access control mechanism within a database. By assigning privileges at a granular level, administrators can ensure that users have the appropriate level of access required for their roles while preventing unauthorized data access and modification. This is especially important for maintaining data confidentiality and complying with data protection regulations.
Significantly, DCL commands are typically carried out by database administrators or users possessing appropriate administrative privileges. Effective use of DCL commands is crucial for maintaining the security and integrity of a database, and they are an integral part of database administration and management.
4. Transactional Control Language (TCL)
Transactional Control Language (TCL), a subset of SQL (Structured Query Language), is dedicated to overseeing transactions within a database management system (DBMS). Transactions are sequences of one or more SQL statements that are treated as a single unit of work. TCL commands provide the means to control the start, end, and outcome of transactions, ensuring data consistency and integrity even in the face of errors or system failures.
TCL commands are particularly important in multi-user environments where multiple users may be accessing and modifying the same data simultaneously. They help maintain the ACID properties of transactions: Atomicity, Consistency, Isolation, and Durability.
Key TCL commands include:
- COMMIT : Used to finalize a transaction and permanently apply its changes to the database. After committing a transaction, its changes become permanent, and subsequent transactions can observe the effects of these alterations.
- Example:
COMMIT;
- Example:
- ROLLBACK : Used to undo changes made during a transaction and restore the database to its previous state. This command is commonly employed in cases of errors or when the transaction requires cancellation.
- Example:
ROLLBACK;
- Example:
- SAVEPOINT : Used to define a point within a transaction to which you can later roll back. Savepoints allow you to divide a transaction into smaller parts for more fine-grained control over rollback actions.
- Example:
SAVEPOINT sp1;
- Example:
- ROLLBACK TO SAVEPOINT : Used to roll back a transaction to a specified savepoint. This permits the reversal of alterations made from the point of establishing the savepoint.
- Example:
ROLLBACK TO SAVEPOINT sp1;
- Example:
- RELEASE SAVEPOINT : Used to remove a savepoint. After releasing a savepoint, rolling back to it is no longer possible.
- Example:
RELEASE SAVEPOINT sp1;
- Example:
TCL commands are crucial for ensuring data integrity and consistency in database systems. They provide a way to group related operations into transactions and handle various scenarios, such as errors or system failures, gracefully. By using TCL commands effectively, developers and database administrators can manage complex interactions between multiple transactions, maintain data accuracy, and ensure the reliability of the database.
Conclusion
In summary, the Database Management System serves as a cornerstone for modern information management. It provides a structured, secure environment to harness, protect, and fully utilize data. From efficiently storing vast datasets to enabling seamless data retrieval, manipulation, and analysis, the DBMS empowers businesses, organizations, and individuals to navigate the complexities of our data-driven world. As we continue to embrace innovation and technological advancements, the DBMS remains a steadfast companion on our journey, ensuring the reliability, integrity, and accessibility of data – the lifeblood of the digital age.



[…] the realm of database management and distributed systems, ACID and CAP principles govern data integrity and availability interplay. Understanding these […]
[…] fundamental terms that often surface in conversations about data organization and manipulation are DBMS (Database Management System) and RDBMS (Relational Database Management System). These acronyms epitomize disparate methodologies […]
[…] today’s data-driven world, Database Management Systems (DBMS) play a pivotal role in organizing, storing, and retrieving vast amounts of information efficiently. […]
[…] for Structured Query Language, is a programming language used to manage and manipulate relational databases. It allows you to create, retrieve, update, and delete data from databases, as well as define their […]
[…] is an open-source relational database management system (RDBMS) that is widely used for storing, managing, and retrieving structured data. It is a crucial […]